
This is a perfect example of banging your head against the wall for a day. Integration information between FreeIPA and just about anything is hard to come by, so I decided to put this short guide together covering it and Nextcloud. This is just a drop in a bucket that desperately needs to be filled. As always, I will endeavour to explain how I figured this out because understanding the how and why is important! Ultimately this investigation resulted in me tracking down a bug in the LDAP app in Nextcloud, and a patch has been merged for the Nextcloud 12 release.
You’ll require a read-only System account in your FreeIPA instance. This is for Nextcloud to bind to for reading users and groups. Basic instructions for creating a user for this purpose are located here on the FreeIPA wiki.
With this in hand and the LDAP / AD Integration app enabled in your Nextcloud instance you can get to configuring. You should be aware of some of your basic configuration settings in FreeIPA, like your basedn which you can find in /etc/ipa/default.conf on your IPA server.
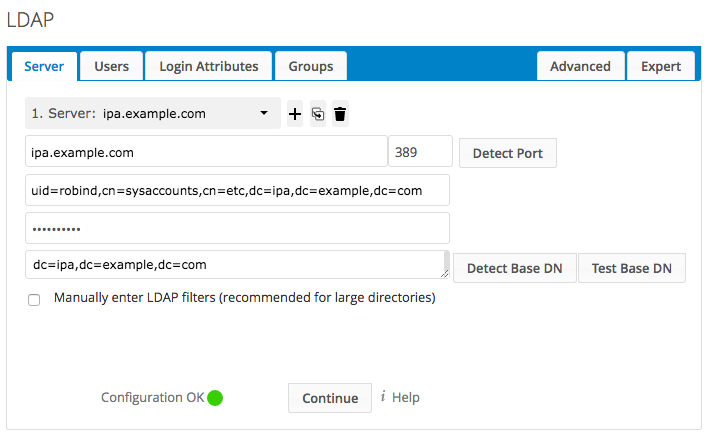
LDAP Server Configuration
The initial configuration page as seen above requires a few different fields of information, specifically
- IPA server’s hostname, and LDAP port (typically 389)
- Your bind user’s DN, which was mentioned earlier
- Its password
- Your directory’s Base DN
For the Users tab, you can limit users to meeting specific criteria. This can be further limited on the Groups tab, so a general setting of ipausers is reasonable.
On the Login Attributes tab you can choose the fields used for logins to Nextcloud. If you want to enable logging in with the user’s email address and have trouble with the LDAP / AD Email Address choice, use the mail attribute in the Other Attributes dropdown.
The Groups tab can be used for limiting user logins to only include those in certain object classes or groups. This is something specific to your setup and needs, so there’s not much to say about this.
From here, some Advanced and Expert tab configuration is required.
Under the Advanced tab, you can input your FreeIPA replica and its port (if that’s how your FreeIPA environment is configured). The important settings for everyone using FreeIPA come next under Directory Settings and Special Attributes.
The settings for the Base User Tree and Base Group Tree can be discovered by utilizing ldapsearch to get some insight into user and group structure.
|
1 2 3 4 5 6 7 8 9 10 11 |
$ ldapsearch -H ldap://ipa.example.com -x -b "dc=ipa,dc=example,dc=com" -D "uid=robind,cn=sysaccounts,cn=etc,dc=ipa,dc=example,dc=com" -W "uid=jsmith" Enter LDAP Password: ... # jsmith, users, accounts, ipa.example.com dn: uid=jsmith,cn=users,cn=accounts,dc=ipa,dc=example,dc=com ... memberOf: cn=ipausers,cn=groups,cn=accounts,dc=ipa,dc=example,dc=com ... ipaUniqueID: aaee4641-6d4a-4e93-b9e5-81cd0db97d1b |
In the above example by searching for one of our user’s UIDs, we can see the user’s DN and DN of its group memberships. There is a lot of other information I have simply cropped out, but another important one is the attribute where the UUID is being stored, which we’ll come back to later.
- User Display Name Field:
displayName - Base User Tree:
cn=users,cn=accounts,dc=ipa,dc=example,dc=comwith the Base DN matching your own - Group Display Name Field:
cn - Base Group Tree:
cn=groups,cn=accounts,dc=ipa,dc=example,dc=comwith the Base DN matching your own
After that, the Special Attributes can be updated.
- At a bare minimum update the Email Field to be
mail - Choose an attribute for the User Home Folder Naming Rule, I’m using
uidwhich for the example user above is jsmith. In a default installation this would have folders being created as/var/ncdata/jsmithfor example, with the files actually being located in/var/ncdata/jsmith/files
With the configuration done up to this point…nothing will work. Turning up debugging will give you no further information, and login attempts with users in your FreeIPA directory will result in a misleading error message about the display name.
|
1 |
LDAP Login: Could not get user object for DN uid=jsmith,cn=users,cn=accounts,dc=ipa,dc=example,dc=com. Maybe the LDAP entry has no set display name attribute? |
It’s worth understanding a little bit about what Nextcloud is doing under the hood with LDAP. Inside the database are two mapping tables (oc_ldap_group_mapping and oc_ldap_user_mapping). This allows an LDAP DN to be linked to something internally appropriate to Nextcloud. The application is meant to do automatic UUID discovery based on some typical attribute names, including FreeIPA’s UUID attribute (which we saw earlier, ipaUniqueID), but some part of this is actually broken, and therein lies the crux of the problem.
I’ve confirmed in packet captures of the LDAP conversation between Nextcloud and FreeIPA that the ipaUniqueID attribute is requested and even receives a valid response with the user’s UUID, but the critical mapping step never actually happens. Without mapping, no users. How do we fix this?
Under the Expert tab we’re offered several fields. To get things working, Override UUID detection is what we’re looking for. By setting this to ipaUniqueID for both Users and Groups, you’ll be up and running, but maybe not as you expected!
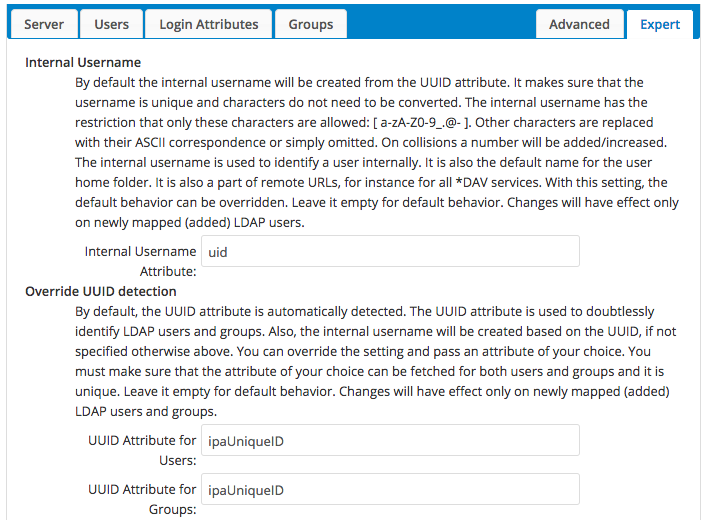
LDAP Server Expert Configuration
When the Internal Username field is left blank, Nextcloud will default to using the UUID. If you were to visit your Users list with this left blank your LDAP user’s Username as shown would be their UUID string which might not be desirable. By setting this instead to uid for example, you will instead have jsmith, for example.
If you’re running a mixed directory, you may want to leave it as the UUID. You probably also want to make sure that your LDAP directory is not serving a user named admin if you do choose to use the uid… (Have not confirmed if that would cause issues, but better safe than sorry)
Once this configuration is done, you should be ready to login to Nextcloud with your FreeIPA users!
Hi
I have added an user like described in: http://www.freeipa.org/page/HowTo/LDAP#System_Accounts, but I cant connect with this user to IPA. It works with a LDAP browser but not with nextcloud… Do I need something more there?
Greetz
Sorry for the very late reply, but start at the bottom and work your way up to try to determine the point of the fault.
Can the two servers reach eachother?
Is LDAP listening on the expected port on your IPA server?
Can you reach the LDAP port on your IPA instance from your Nextcloud server?
Can the Nextcloud server perform any LDAP queries to IPA?
Does the LDAP user account work from the commandline of the Nextcloud server?
What error messages are returned?
NextCloud 20.05 and FreeIPA V4 on CentOS7
FreeIPA is fworking fine with other Web-apps (pfSense and other). I can find anything using ldapsearch and my bind user. However, with NextCloud 20.05 I’m getting this message no matter what:
{“reqId”:”YAH-4jJXfxPdTzUBDa6yPAAAAAA”,”level”:2,”time”:”2021-01-15T20:49:39+00:00″,”remoteAddr”:”10.0.xx.xx”,”user”:”–“,”app”:”user_ldap”,”method”:”POST”,”url”:”/index.php/login”,”message”:”LDAP Login: Could not get user object for DN uid=user,cn=users,cn=accounts,dc=xxxxxxx,dc=xx. Maybe the LDAP entry has no set display name attribute?”,”userAgent”:”Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:84.0) Gecko/20100101 Firefox/84.0″,”version”:”20.0.5.2″}
{“reqId”:”YAH-4jJXfxPdTzUBDa6yPAAAAAA”,”level”:2,”time”:”2021-01-15T20:49:39+00:00″,”remoteAddr”:”10.0.92.63″,”user”:”–“,”app”:”no app in context”,”method”:”POST”,”url”:”/index.php/login”,”message”:”Login failed: user (Remote IP: 10.0.xx.xx)”,”userAgent”:”Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:84.0) Gecko/20100101 Firefox/84.0″,”version”:”20.0.5.2″}
NextCloud says LDAP configuration is OK – here it is
Manually enter LDAP filters (recommended for large directories)
LDAP Query on Users tab: (&(objectclass=posixaccount))
LDAP Query on Login Attributes tab: (&(objectClass=posixaccount)(uid=%uid))
LDAP Query on Groups tab (&(objectClass=posixgroup)(cn=nextcloud))
All green and all check returns OK
Advanced tab:
User Display Name Field: displayname
2nd User Display Name Field:
Base User Tree: cn=users,cn=accounts,dc=xxxxxxx,dc=xx
User Search Attributes:
Group Display Name Field: cn
Base Group Tree: cn=groups,cn=accounts,dc=xxxxxxx,dc=xx
Group-Member association: gidNumber
Email Field: mail
User Home Folder Naming Rule: uid
Expert tab:
Internal Username: uid
UUID Attribute for Users: ipaUniqueID
UUID Attribute for Groups: ipaUniqueID
Still no luck 🙁
Have you browsed the directory as the NextCloud LDAP user and checked that the displayName attribute is visible on users your filter returns?
Just: thanks so much for this!
Hey,
first thank u very much for that guide! It really helped me and it worked perfectly.
The only thing i cant accomplish, is to get the mail adresses from freeipa into my nextcloud. Do u have any Idea what i may could done wrong? I changed the field under advance to mail but it wont help.
Did you only want to display the email, or have it used for login? Using ldapsearch take a look at the attributes of one of your users and see what attribute the email address is contained in.