If you have plans to make use of the audit system in RHEL and its clones, you may decide to use pam_tty_audit. A lot of the top hits on Google will recommend enabling the module in /etc/pam.d/system-auth-ac, but because of changes related to having better support for HIDs like fingerprint scanners, it should actually exist in /etc/pam.d/password-auth-ac, which is included by /etc/pam.d/sshd and others. One other complaint is that it logs passwords, but a patch was implemented in an update to RHEL 6 to address this.
Add the following line to the end of /etc/pam.d/password-auth-ac to enable keystroke logging for all users on a default RHEL, CentOS or Scientific Linux 6 server:
session required pam_tty_audit.so enable=*
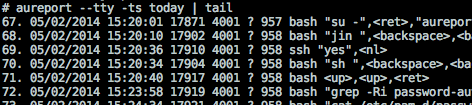
The raw audit log can then be viewed at /var/log/audit/audit.log (which includes other audit events) or output in a somewhat friendlier format using aureport as root.
aureport --tty -ts today
The audit system caches based on settings in /etc/audit/auditd.conf, so it could take some time before you see audit logs for user activity. Check its man page for further information